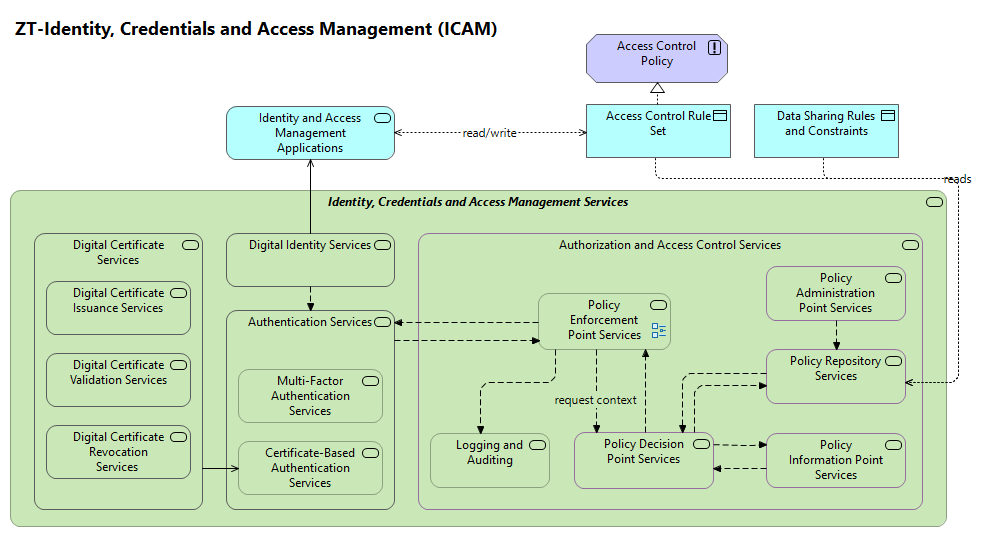
| |
|
Identity, Credentials and Access Management Services |
Authentication Services |
| |
|
Identity, Credentials and Access Management Services |
Digital Certificate Services |
| |
|
Identity, Credentials and Access Management Services |
Authorization and Access Control Services |
| |
|
Identity, Credentials and Access Management Services |
Digital Identity Services |
| |
|
Digital Identity Services |
Authentication Services |
| |
|
Digital Identity Services |
Identity and Access Management Applications |
| |
|
Authentication Services |
Policy Enforcement Point Services |
| |
|
Multi-Factor Authentication Services |
Authentication Services |
| |
|
Certificate-Based Authentication Services |
Authentication Services |
| |
|
Digital Certificate Services |
Digital Certificate Issuance Services |
| |
|
Digital Certificate Services |
Digital Certificate Validation Services |
| |
|
Digital Certificate Services |
Digital Certificate Revocation Services |
| |
|
Digital Certificate Services |
Certificate-Based Authentication Services |
| |
|
Authorization and Access Control Services |
Logging and Auditing |
| |
|
Authorization and Access Control Services |
Policy Decision Point Services |
| |
|
Authorization and Access Control Services |
Policy Information Point Services |
| |
|
Authorization and Access Control Services |
Policy Repository Services |
| |
|
Authorization and Access Control Services |
Policy Enforcement Point Services |
| request context |
|
Policy Enforcement Point Services |
Policy Decision Point Services |
| |
|
Policy Enforcement Point Services |
Logging and Auditing |
| |
|
Policy Enforcement Point Services |
Authentication Services |
| |
|
Policy Administration Point Services |
Policy Repository Services |
| |
|
Policy Decision Point Services |
Policy Enforcement Point Services |
| |
|
Policy Decision Point Services |
Policy Information Point Services |
| |
|
Policy Decision Point Services |
Policy Repository Services |
| |
|
Policy Information Point Services |
Policy Decision Point Services |
| |
|
Policy Repository Services |
Policy Decision Point Services |
| reads |
|
Policy Repository Services |
Access Control Rule Set |
| |
|
Policy Repository Services |
Data Sharing Rules and Constraints |
| |
|
Access Control Rule Set |
Access Control Policy |
| |
|
Identity and Access Management Applications |
Access Control Rule Set |